Security Features
Our platform provides safe and secure access and flexible access control and supports integration with all industry-standard security solutions.
Authentication
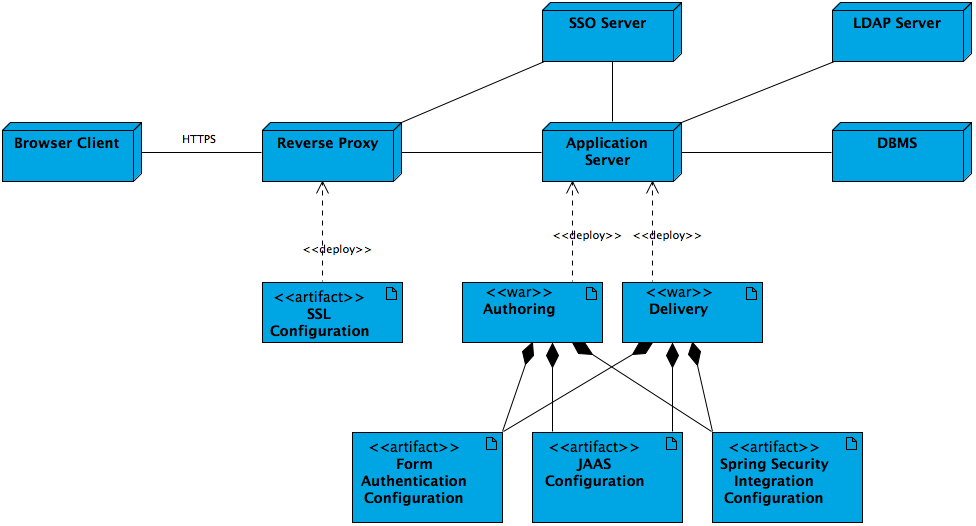
Hippo CMS/DX supports multiple authentication methods and offers several integration options to leverage existing solutions in your enterprise architecture.
Our standard authentication module is based on JAAS and supports form-based authentication (authoring and delivery) and HTTP basic authentication (delivery only). Users and encrypted passwords are stored in the content repository. Optionally authentication against and synchronization with an LDAP server can be configured.
The authentication module is extensible or replaceable through JAAS or our Spring Security Integration plugin.
Two-factor authentication is supported out-of-the-box through integration with Duo Security.
Single sign-on (SSO) scenarios are supported using a reverse proxy which redirects browser clients to a central Enterprise SSO server for authentication. After authentication, the client is provided a valid security token and is redirected to the originally requested page.
HTTPS support is seamless in both the authoring environment and the delivery tier: no configuration at application level is needed.
Authorization and Workflow
Authorization is role-based and can be applied to so-called security domains which can be configured to include or exclude any possible subset of content, such as channels, folders, content types or even fields within content types.
Control over your publication process is provided by our standard workflow which enables content to be prepared by authors and then reviewed by editors before publication to your channels. Scheduled publication enables working with embargoed content.
Within your publication channels, webmasters can configure URLs, pages, content mappings, components, and templates.
Audit Trail
Hippo CMS/DX maintains a full audit trail of all user activity and content changes. All login attempts (successful or unsuccessful) and all workflow operations are logged. Content items have an automatically maintained version history detailing each published change and can be reverted to any previously published version.
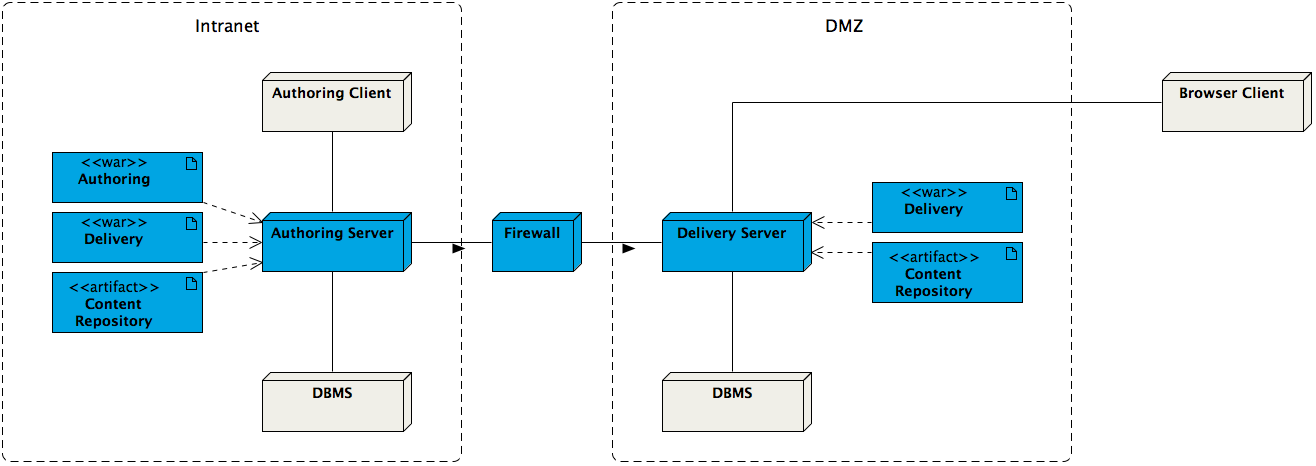
DMZ Support
Support for a demilitarized zone (DMZ) is provided through content replication. In a typical setup, a separate cluster running content repository and delivery tier are placed in the DMZ, in addition to the usual cluster running content repository, authoring application and delivery tier behind a firewall. Content authoring and preview take place exclusively behind the firewall. Only selected published content is replicated automatically to the second content repository in the DMZ. The separate delivery tier in the DMZ can only access the replicated content.
Application Security
Hippo makes a continuous effort, including regular third-party security audits, to make sure Hippo CMS/DX is protected against known methods of attack. A checklist is provided to verify a delivery tier implementation against the OWASP Top 10 Most Critical Web Application Security Risks.
In the rare case that a potential vulnerability is identified, a thorough and well-defined process is in place to assess, verify, and fix the issue, and inform customers and the community.

